We simplify digital transformation.
Customer Stories
We take the world’s best cloud, security and business apps, streamline them, pre-configure them, automate their deployment, to make them simple and affordable. In this way, we help SMBs to think bigger and realise their dreams.

Productivity company moves to Azure for efficiency gains
ANS helps T Cards move to Azure to provide scalability and efficiency as the visual planning boards company expands operations.
Read more
eCloud gives HR platform resilience
HR software platform company moves to eCloud for greater resilience and availability.
Read moreSecurity
Receive the highest level of threat monitoring with enterprise grade cloud security.
Managed XDR
As a managed service, we can take full responsibility for your threat prevention, detection and response.
Security COE
Tap into a rich pool of security skills and resources as and when they need them, without building in-house.
Customer Stories

Secure cloud platform for emergency services
ANS deploys secure platform to enable Police, NHS, Councils, Armed Forces, and coast guards to securely share information for coordinating emergency responses during major incidents.
Read more
3 security breaches you’re glad you didn’t face
Another season of swiping and spending is over and retailers across the UK are relishing...
Read moreCustomer Stories
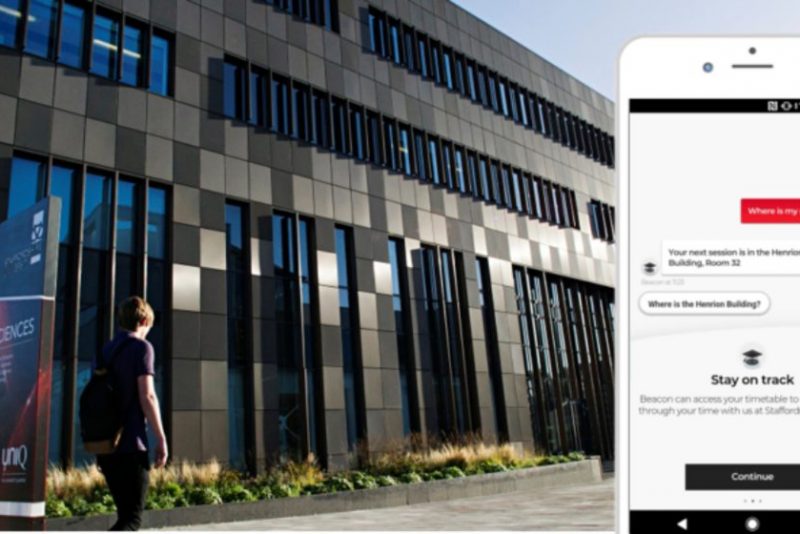
Staffordshire University creates future blueprint for student success using artificial intelligence
Staffordshire University has teamed up with leading Cloud Services Provider, ANS Group to become the...
Read more
London Borough builds modern data platform.
ANS advises London Borough of Islington on Azure strategy to develop a modern data platform that improves outcomes for citizens.
Read moreDynamics 365 Sales
Let us achieve your sales goals affordably and efficiently.
Dynamics 365 Marketing
Engage prospects and customers one-on-one and at scale with timely, personalised content.
Dynamics 365 Field Service
Empower your service teams and boost customer satisfaction.
Dynamics 365 Customer Service
Empower agents to resolve cases faster and delight your customers with ease.
Customer Stories
Customer Stories

Howdens partners with ANS to improve its Lead Management App.
Howdens engaged with ANS to update its lead management application and improve customer onboarding capabilities....
Read more
Highlights of Gartner’s new report on Low Code
By Chris Huntingford and Jason Earnshaw , Our Low Code practice leads. Our Low Code...
Read moreSolutions for every type of organisation

Enterprise
We automate digital transformation barriers, optimise cloud security and modernise business apps for faster and more valuable insights.

Public Sector
We simplify public sector digital transformation with cloud migration, application modernisation, security, social value, and data insights. Benefit from increased organisational agility and automated processes.

Channel
We offer our cloud, security, and digital services to enable all our partners to build their perfect proposition and generate additional revenue.

SMB
We simplify cloud platforms for a tailored solution. Modernise your SMB with our enterprise-grade technology. Our Security Checked engineers prevent cyber threats 24/7.
Every organisation should have access to the best cloud and digital technology and know-how. Because every organisation, large or small, has the right to realise their dreams. This is our mission.
£2m to help you reach your digital ambitions.
For those companies with big digital ambitions, but not the funds or expertise to achieve them, there is the ANS Ambition Fund.
Find out moreUnrivalled partnerships.
Useful resources.
Insight, opinions, news and customer stories from the team at ANS.
 Insight
Insight
5 top tips to successful cloud adoption
 Customer Story
Customer Story
eCloud gives HR platform resilience
 Insight
Insight
11 Ways to Boost Dynamics 365 CRM User Adoption

Diversity is our DNA.
We are constantly working to make ANS a fully inclusive workplace where our people can be their amazing true selves every day.

Why we exist.
Every organisation should have access to the best digital transformation technology, people, and processes. We fundamentally believe every organisation, large or small, has the right to realise their dreams and think bigger.
So we’ve made this our mission.
Talk to us.
To find out more about ANS or talk to one of our experts, please don’t hesitate to get in touch.